Industry 4.0 for machine tools
The aim of the project "Anonymization4Optimization" from the VDW working group 2 "Control Technology" is the anonymization of process and machine data in order to make data processing in the cloud usable in the machine tool sector. The Institute for Machine Tools and Industrial Management (iwb) at the Technical University of Munich and the Fraunhofer Institute for Applied and Integrated Security (AISEC) in Garching near Munich are creating a common understanding of security for cloud-based data processing by machine tool operators and manufacturers.
Data processing in the cloud
In the course of the so-called fourth industrial revolution, production plants and production systems are becoming increasingly connected and more and more artificial intelligence is incorporated. The long-term goal is to enable self-organized production systems, thus creating an optimized value-added chain. However, this will only be possible if the production systems can exchange data and communicate with each other. In addition to internal communication, external communication to cloud systems is particularly useful. Taking a machine tool as an example, this would mean that computationally expensive calculations are outsourced to the cloud computing center, since current machine controls cannot perform these calculations in real time. If a developer of machine tools or components has access to certain data during the use of his product, he can use this data to optimize the machine in the next generation in terms of hardware or current software. At the same time, there is also added value for the machine user, who can increase productivity or predict component failure based on a cloud-based process analysis.
Anonymization and IT security
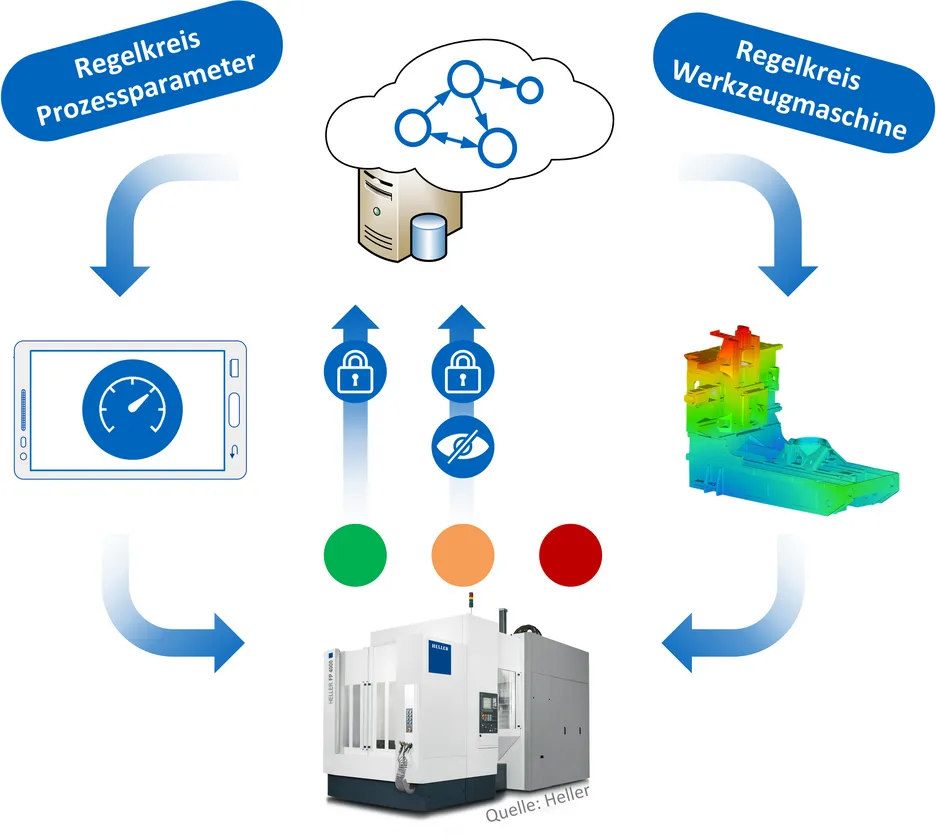
In order to close and implement this control loop of machine tool optimisation, the trust of machine tool operators in data protection and IT security in particular must be guaranteed. In order to increase the willingness of machine operators to transfer available sensor or system data to cloud-based computing centers, it must be ensured that no sensitive information leaves the company. The "Anonymization4Optimization" research project addresses this area of conflict by anonymizing the data while it is still in the company and then transferring it encrypted to the cloud. At the same time, the anonymized data must allow meaningful evaluations by the manufacturer. This control loop is shown schematically in Figure 1. In advance, it is defined which data is to be regarded as insensitive, sensitive and critical (shown in green, orange and red in Figure 1). In particular, the technological know-how and intellectual property of the machine operator must be protected. Here, the possible reconstruction of critical data from non-critical data must also be considered. A proper handling of anonymized data and the integrity of the functions in the cloud and the machine tool should be certified by security techniques. This can ensure that the machine developer receives useful data which can be used for optimisation, for example with regard to dynamic behaviour. It is ensured that the sensitive data of the machine user is protected.